Jan. 20, 2026 /PRNewswire/ — The Q4 2025 Gen Threat Report highlights a significant shift in cybercrime, where fraudulent advertisements and deepfake content have become the primary methods for targeting consumers. These findings indicate that attackers are increasingly exploiting trusted social media platforms like Facebook and YouTube to host fake online shops and deceptive investment schemes. Rather than using complex technical exploits, modern scams trick individuals into performing routine digital actions, such as clicking links or scanning QR codes, to compromise their data. The report also identifies GhostPairing attacks and a sharp rise in identity-related breaches as growing risks that bridge the gap between mobile and desktop devices. Ultimately, the data warns that malvertising has evolved into a sophisticated tool that allows threats to blend seamlessly into everyday internet browsing. Continue reading
Tag Archives: Computer security
Cybersecurity Forecast 2026: The Rise of AI Agents, Persistent Extortion, and Evolving Nation-State Tactics
Dec. 29, 2025 /Mpelembe Media/ — The Cybersecurity Forecast 2026 report by Google Cloud examines the anticipated evolution of digital threats, primarily focusing on the transformative role of artificial intelligence. It describes how adversaries will increasingly use AI agents for automated attacks and sophisticated social engineering, while defenders will adopt similar technology to enhance security operations. Beyond AI, the analysis highlights the persistent danger of ransomware and the expansion of cybercrime into the blockchain and virtualisation sectors. The document also evaluates the strategic motivations of nation-state actors from Russia, China, Iran, and North Korea as they pursue global espionage and disruption. Ultimately, the report serves as a guide for organisations to modernise their identity management and governance frameworks in response to these emerging risks. Continue reading
There’s no place like Chrome
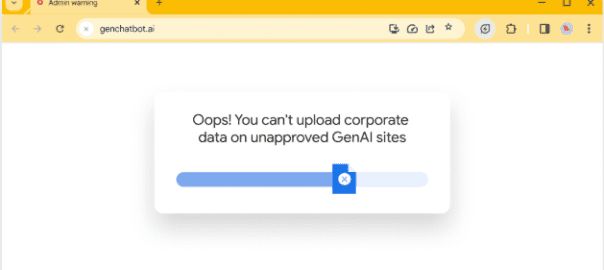
Dec. 25, 2025 /Mpelembe Media/ — Chrome Enterprise Premium is a specialized web browser solution designed to enhance corporate security through a Zero Trust architecture. By acting as a central enforcement point, it provides businesses with advanced threat protection against malware, phishing, and malicious websites. The platform features robust data loss prevention tools that allow administrators to restrict sensitive actions like uploading, printing, or downloading on various devices. It simplifies endpoint management by offering real-time visibility and context-aware access controls without requiring complex software installations. Ultimately, this service enables IT teams to secure a modern workforce while maintaining high levels of productivity and seamless integration with existing tools. Continue reading
Privacy risks associated with the Epstein Library
Dec. 19, 2025 /Mpelembe Media/ — This official webpage serves as a public repository hosted by the United States Department of Justice specifically for the Epstein Library. It provides access to a collection of legal and government documents, including court records and disclosures released under the Freedom of Information Act. Users can download various electronic files organized into specific datasets, though the agency warns that some sensitive or private information may remain despite efforts to censor it. The site also includes a privacy notice requesting that the public report any inadvertently published personal details to a dedicated government email address. Ultimately, this digital archive functions as a transparency tool for reviewing materials related to specific high-profile legal matters. Continue reading
VIPRE Q3 2025 Email Threat Landscape Report
The report provided by VIPRE Security Group concerning their Q3 2025 Email Threat Landscape Report, which details how cybercriminals are using increasingly sophisticated methods to bypass traditional email defences. The report reveals that commercial clutter makes up the largest proportion of email volume and is intentionally used to desensitise users, enabling malicious emails like phishing attempts to blend in. Key findings highlight that attackers frequently exploit compromised URLs or open redirects and are strategically targeting Outlook and Google mailboxes, which together constitute ninety per cent of observed phishing attacks. Furthermore, the report notes emerging technical trends such as the use of Fetch API for credential exfiltration and the abuse of Apple’s TestFlight platform to distribute malicious iOS applications, while acknowledging that geographic dispersion across spam-sending markets is making traditional IP blocking ineffective. Overall, the source stresses that organisations must adopt equally adaptive and layered defences to counter the evolving threat landscape. Continue reading
Geopolitical and Digital Disruption Risk Trends
“Risk in Focus,” by The Institute of Internal Auditors’ Internal Audit Foundation, highlights significant shifts in the global risk landscape. The research, based on feedback from over 4,000 internal audit professionals, indicates that geopolitical uncertainty and digital disruption have seen the largest increases in risk levels this year. Despite this, cybersecurity remains the highest-rated risk worldwide. The report also notes a gap between the perceived high risk of areas like geopolitical uncertainty and digital disruption and their relatively lower audit priority ratings globally, urging practitioners to address these growing risks proactively through related areas like business resilience and regulatory change. Continue reading
Security delivered for working people as UK-US ties strengthened with new Google Cloud partnership for classified information sharing
From:
Ministry of Defence and The Rt Hon John Healey MP
Published
12 September 2025
UK – US defence and security ties enhanced through major deal with Google Cloud – delivering the Government’s Plan for Change.
Continue reading
OpenSSF Launches Free Course to Prepare Developers for the EU Cyber Resilience Act
The Open Source Security Foundation (OpenSSF), in collaboration with LF Education, announces the general availability of LFEL1001, a free online course designed to help software developers understand and prepare for the requirements of the European Union (EU) Cyber Resilience Act (CRA). Continue reading
Cybersecurity Priorities 2025
Jan. 23, 2025 /Mpelembe Media/ — Info-Tech Research Group’s 2025 Security Priorities report identifies key cybersecurity challenges, including the rise of AI-powered threats and quantum computing. The report, based on extensive research, advises organisations to proactively manage risks by operationalising AI security, strengthening identity management, and building resilient vendor security practices. Continue reading
UK Banking IT Failures and Security Concerns
Jan. 7, 2025 /Mpelembe Media/ — New research from the UK reveals that a significant portion of the British public is keeping cash on hand due to concerns about banking IT failures. One in four Brits report this behaviour, highlighting a growing distrust in digital banking systems. Concerns centre on the frequency of IT outages and the potential for data breaches, impacting consumer confidence. The research underscores the need for banks to improve IT security and transparency to reassure customers. Continue reading